Turning Vision into Intelligence
Traditional CCTV systems watch. Our Intelligent Surveillance Systems think.
At Mentor Infocomm, we combine high-definition imaging, AI-driven video analytics, real-time alerts, and centralized control to give you more than just visibility — we give you foresight.
From smart cities to critical infrastructure, from corporate campuses to industrial sites, our intelligent surveillance platforms transform raw footage into actionable intelligence — protecting what matters most while improving efficiency and peace of mind.
Smarter Eyes for Smarter Security
Our cameras don’t just record — they interpret. Equipped with AI at the edge, they detect, analyze, and react faster than ever before.
Every frame captured delivers clarity and context:
- Ultra-HD and 4K imaging ensure not a single detail is missed.
- Thermal and audio sensors detect what eyes can’t — from low-light movement to breaking glass or gunshots.
- On-device analytics process data in real time, cutting server load and speeding response.
It’s not surveillance. It’s situational awareness — redefined.
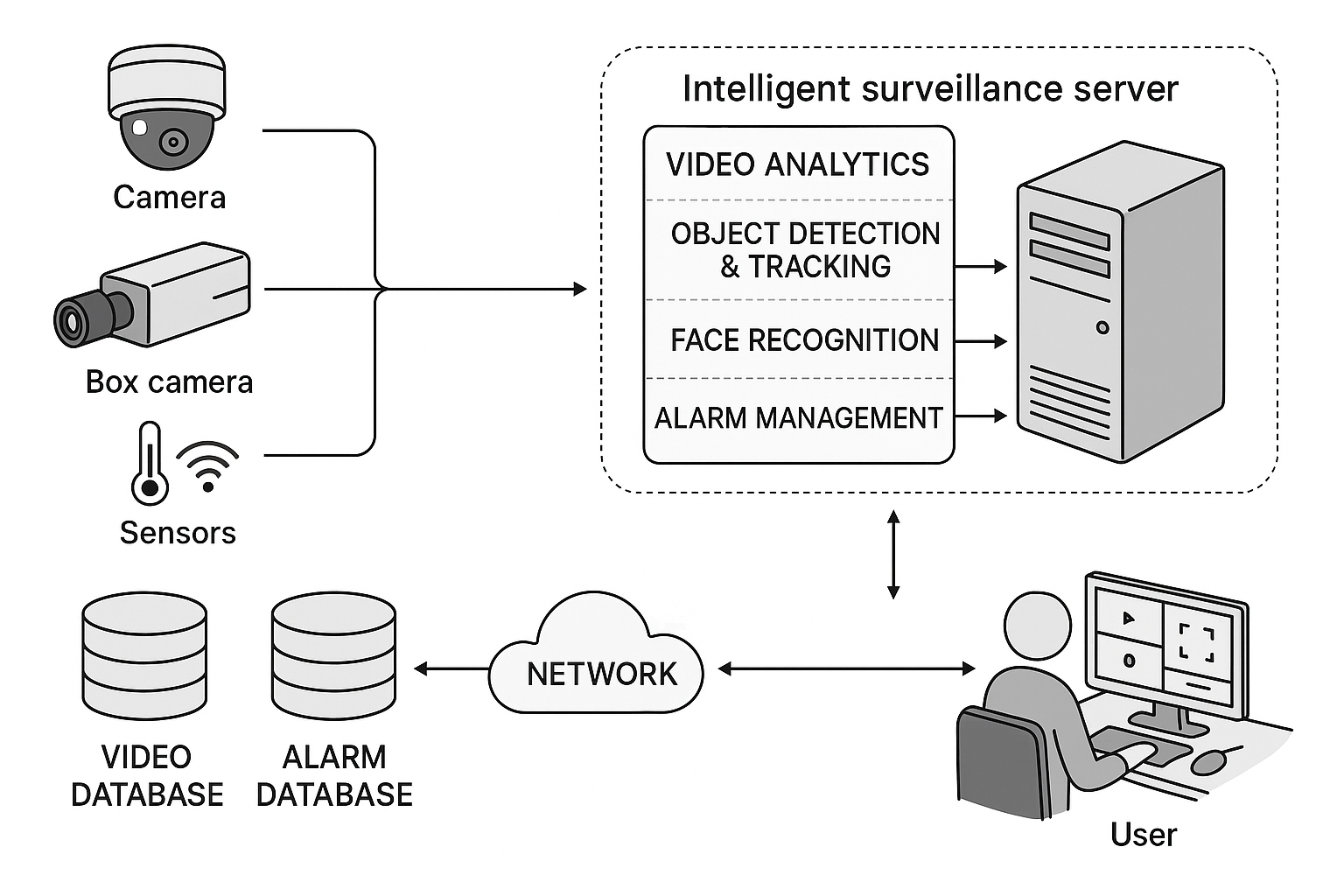
The Brain Behind the Eyes
Behind every intelligent camera is a powerful brain — your NVRs and servers. These systems manage, analyze, and store vast amounts of video data with precision and reliability.
Designed for high availability, they combine large storage capacity, high-speed networking, and real-time AI processing — enabling your team to track, review, and respond to incidents as they unfold.
No lag. No gaps. No compromises.
From Monitoring to Understanding
Here’s where AI video analytics turns observation into prevention. Our systems don’t just show what happened — they interpret what’s happening, as it happens.
They detect objects, recognize faces, track license plates, and identify suspicious movements — automatically distinguishing between normal behavior and potential threats. Unattended baggage, restricted access violations, or unusual crowd activity trigger instant alerts, helping your security team act before incidents escalate.
With AI-driven surveillance, you move from passive watching to proactive protection.
Intuitive Control at Your Fingertips
Security shouldn’t feel complicated. Our Video Management Software (VMS) brings everything together — cameras, alerts, analytics, and playback — into a single, intuitive dashboard.
Operators can view live feeds, manage notifications, search incidents, and access systems remotely — all through a unified interface accessible from desktop, mobile, or tablet.
Whether you’re on-site or on the move, you’re always in control.
Built for Reliability, Designed for Scale
Surveillance is mission-critical — and we treat it that way. Every system we deploy is designed to perform flawlessly 24/7, with scalability and security at its core.
We combine edge and cloud computing for speed and resilience, integrate with existing access control or alarm systems, and ensure compliance with the latest data privacy and cybersecurity standards.
From a single facility to a city-wide network, your system grows as your needs do — seamlessly and securely.
24/7 Awareness. Anywhere. Anytime.
Your world doesn’t stop, and neither do we. With remote monitoring, your team receives real-time alerts, can replay footage instantly, and even control cameras from anywhere.
When something happens, you’ll know — immediately.
Why Mentor Infocomm
Choosing Mentor Infocomm means choosing a partner that understands both technology and trust. We deliver end-to-end surveillance ecosystems — from intelligent cameras to cloud analytics — backed by proven reliability and 24/7 support.
We promise:
Smarter intelligence. Fewer false alarms. Stronger protection. And complete peace of mind — all day, every day.
Ready to Turn Surveillance into Security Intelligence?
Let’s build a system that doesn’t just see — it understands. Connect with Mentor Infocomm to design your next-generation surveillance solution today.




 Call Now
Call Now

